As described by a Kubernetes Storage Class, a persistent volume (PV) in Kubernetes is an object that enables pods to access persistent storage on a storage device. As opposed to normal volumes, which are transient, PVs offer stateful application use cases since they are persistent. Furthermore, a PV is a resource object in a Kubernetes cluster that survives the destruction of the pods that use it.
Requirements for backing storage
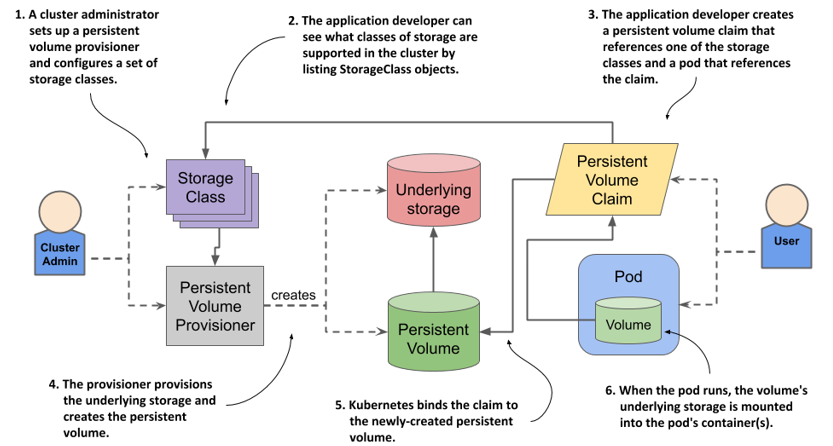
The storage class for Kubernetes persistent volume should interact with different types of storage and handle persistent volume objects to allow users to store data on the persistent volume independently. The storage class should also be able to handle claims. A valid DNS subdomain must back the persistent volume object.
Cloud Volumes ONTAP on Azure must run in the same Azure region as the Kubernetes cluster. Kubernetes clusters cannot use Cloud Volumes ONTAP. Using Cloud Volume ONTAP on Azure for backing a persistent volume is required. The CSI driver should support snapshot-based backup.
In addition, a PV can specify a node affinity and restrict access to certain nodes. A PV’s node affinity will affect how pods are scheduled for them. You can read more about this in the persistent volume API reference. You can also find the name of the PVC bound to your PV. This PVC must have the same storage class name as your PVC. In addition, the name must be a valid DNS subdomain name.
The persistent volume feature in Kubernetes allows you to manage data flexibly without worrying about getting lost or accidentally deleted. The feature also makes it easier for you to manage backups, performance, and storage capacity allocation.
Issues with Kubernetes persistent volume
A persistent volume is a storage asset that persists across restarts. This type of storage resource is used for data storage in Kubernetes clusters. It is an excellent choice for a variety of applications. This type of storage resource supports both internal and external storage.
Persistent volumes provide workloads with storage that survives restarts and scheduling to different nodes. However, persistent volumes can fail to attach or mount correctly. If this occurs, you will receive an error message saying, “FailedAttachVolume failed.” In addition, this message will list any other possible causes for the failure.
Currently, there are three main options for persistent volumes. First, you can mount a volume as read-only by many nodes or read-write by just one pod. For the latter, use ReadWriteOncePod access mode. Using this option, you can ensure that a single pod can read and write PVCs.
Another option for persistent volumes is to use block devices. Block devices, by contrast, can be empty. Kubernetes will create a filesystem on a block device before mounting it. However, this isn’t recommended for production use because block devices tend to cause more trouble.
The name of the storage class object is important. You don’t want to bind a PV to a PVC that lacks a storage class name. However, if you have a PV with a storage class named””, you can change it later. However, this will cause the new PVC to no longer bind to PVs with a storage class named “”.
Security implications
Persistent Volumes (PV) are containers’ storage resources. These volumes can be created and destroyed by a cluster. In addition, a cluster can set the reclaim policy, which instructs Kubernetes on what to do with the persistent volume after it has been released to manage it. There are three different reclaim policies: Retain, Recycle, and Delete. The first option, Destroy, removes the Persistent Volume object from Kubernetes and the associated storage asset, while the second one, Recycle, performs a basic volume scrub.
NFSv3 assumes that all clients authenticate and authorize before accessing the data on a volume. Therefore, NFS3 could arbitrarily specify a volume’s uid/gid. Additionally, NFSv3 does not enforce the principle of a single uid per user, meaning that any pod in the same namespace could use it. In contrast, Kerberos restricts access to a volume’s data to authorized users exclusively.
PVCs’ requirements can be satisfied through dynamic provisioning. This option is used when no static PVs are compatible with the PVC. In dynamic provisioning, a user creates a PVC request specifying the amount of storage and access modes, and then the system tries to locate a matching PV. Unlike static PVs, dynamic PVs are exclusive once bound.
Using persistent volume in Kubernetes clusters has some security implications. First, it can lead to misconfiguration errors that aren’t apparent until runtime. These issues include hidden malware activation, privilege escalation, and weak access controls. These vulnerabilities can lead to prolonged application downtime and data loss.





Comments